
What is it ?
Cybersecurity is the protection of internet-connected systems, including hardware, software and data, from cyberattacks.
In a computing context, security comprises cybersecurity and physical security -- both are used by enterprises to protect against unauthorized access to data centers and other computerized systems. Information security, which is designed to maintain the confidentiality, integrity and availability of data, is a subset of cybersecurity.
What are the consequences of a cyber attack?
Cyber attacks can disrupt and cause considerable financial and reputational damage to even the most resilient organisation. If you suffer a cyber attack, you stand to lose assets, reputation and business, and potentially face regulatory fines and litigation – as well as the costs of remediation.
The UK government's Cyber Security Breaches Survey 2018 found that the average cost of a cyber security breach for a large business is £22,300 and for a small to medium-sized business is £2,310.
The cyber threats organisations face
Although larger organisations tend to have a realistic appreciation of the cyber threats they face, many small to medium-sized enterprises are unclear about the ways in which they’re vulnerable, and as many as 45% mistakenly think they’re not a viable target.
In fact, all Internet-facing organisations are at risk of attack. And it’s not a question of if you’ll be attacked, but when you’ll be attacked. The majority of cyber attacks are automated and indiscriminate, exploiting known vulnerabilities rather than targeting specific organisations. Your organisation could be being breached right now and you might not even be aware.
What is cybersecurity all about?
A successful cybersecurity approach has multiple layers of protection spread across the computers, networks, programs, or data that one intends to keep safe. In an organization, the people, processes, and technology must all complement one another to create an effective defense from cyber attacks.People
Users must understand and comply with basic data security principles like choosing strong passwords, being wary of attachments in email, and backing up data. Learn more about basic cybersecurity principles.
Processes
Organizations must have a framework for how they deal with both attempted and successful cyber attacks. One well-respected framework can guide you. It explains how you can identify attacks, protect systems, detect and respond to threats, and recover from successful attacks. Watch a video explanation of the NIST cybersecurity framework.
Technology
Technology is essential to giving organizations and individuals the computer security tools needed to protect themselves from cyber attacks. Three main entities must be protected: endpoint devices like computers, smart devices, and routers; networks; and the cloud. Common technology used to protect these entities include next-generation firewalls, DNS filtering, malware protection, antivirus software, and email security solutions.
Why is cybersecurity important?
In today’s connected world, everyone benefits from advanced cyberdefense programs. At an individual level, a cybersecurity attack can result in everything from identity theft, to extortion attempts, to the loss of important data like family photos. Everyone relies on critical infrastructure like power plants, hospitals, and financial service companies. Securing these and other organizations is essential to keeping our society functioning.
Everyone also benefits from the work of cyberthreat researchers, like the team of 250 threat researchers at Talos, who investigate new and emerging threats and cyber attack strategies. They reveal new vulnerabilities, educate the public on the importance of cybersecurity, and strengthen open source tools. Their work makes the Internet safer for everyone.
Types of cybersecurity threats
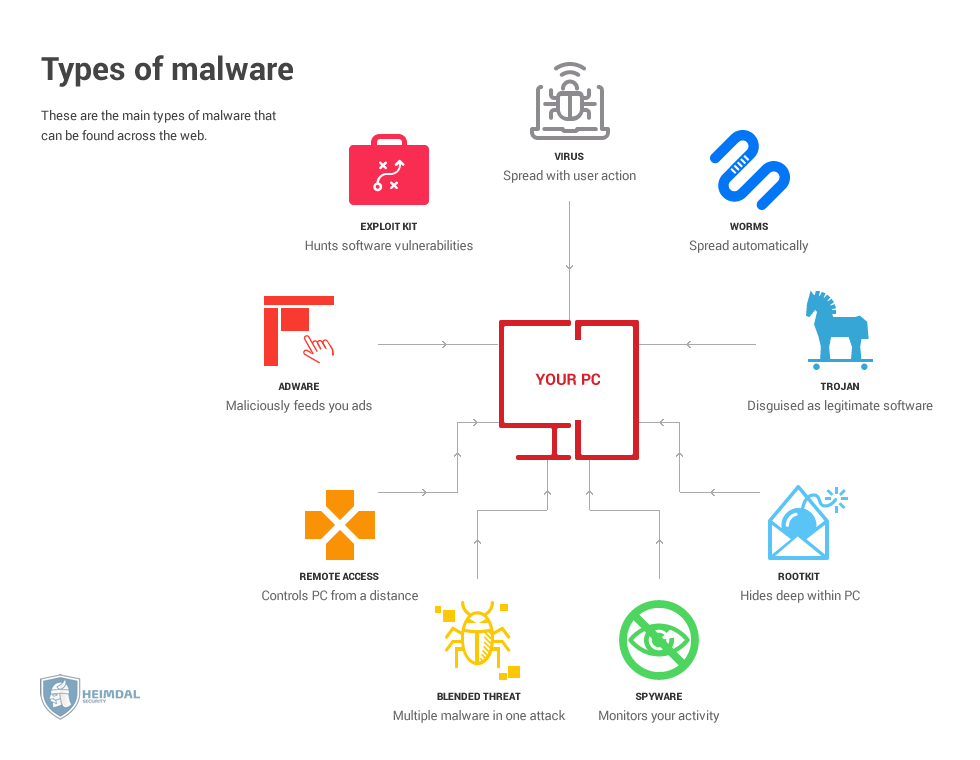
Types of Cyber Threats
In 2012, Roger A. Grimes provided this list, published in Infoworld, of the top five most common cyber threats:- Social Engineered Trojans
- Unpatched Software (such as Java, Adobe Reader, Flash)
- Phishing
- Network traveling worms
- Advanced Persistent Threats
But since the publication of this list, there has been widespread adoption of several different types of game-changing technology: cloud computing, big data, and adoption of mobile device usage, to name a few.
In September 2016, Bob Gourley shared a video containing comments from Rand Corporation testimony to the House Homeland Security Committee, Subcommittee on Cybersecurity, Infrastructure Protection and Security Technologies regarding emerging cyber threats and their implications. The video highlights two technology trends that are driving the cyber threat landscape in 2016:
- Internet of things – individual devices connecting to internet or other networks
- Explosion of data – stored in devices, desktops and elsewhere
Today, the list of cyber threats may look more like this, and cyber threats are typically composed of a combination of these:
- Advanced Persistent Threats
- Phishing
- Trojans
- Botnets
- Ransomware
- Distributed Denial of Service (DDoS)
- Wiper Attacks
- Intellectual Property Theft
- Theft of Money
- Data Manipulation
- Data Destruction
- Spyware/Malware
- Man in the Middle (MITM)
- Drive-By Downloads
- Malvertising
- Rogue Software
- Unpatched Software
Unpatched software, seemingly the simplest vulnerability, can still lead to the largest leaks, such as the case of Panama Papers.
Sources of Cyber Threats
In identifying a cyber threat, more important than knowing the technology or TTP, is knowing who is behind the threat. The TTPs of threat actors are constantly evolving. But the sources of cyber threats remain the same. There is always a human element; someone who falls for a clever trick. But go one step further and you will find someone with a motive. This is the real source of the cyber threat.
For example, in June of 2016, SecureWorks revealed tactical details of Russian Threat Group-4127 attacks on Hillary Clinton's presidential campaign emails. Then, in September, Bill Gertz of The Washington Timesreported on another cyber attack on Hillary Clinton's emails, presumed to be the work of "hostile foreign actors," likely from either China or Russia. There currently exists a U.S. policy on foreign cyber threats known as "deterrence by denial." In this case, denial means preventing foreign adversaries from accessing data in the U.S.
But not all cyber threats come from foreign countries. Recently, Pierluigi Paganini @securityaffairs reported that police arrested two North Carolina men who are alleged to be members of the notorious hacking group called 'Crackas With Attitude' which leaked personal details of 31,000 U.S. government agents and their families.
Most Common Sources of Cyber Threats
- Nation states or national governments
- Terrorists
- Industrial spies
- Organized crime groups
- Hacktivists and hackers
- Business competitors
- Disgruntled insiders
Cyber Threat Intelligence is Necessary for Enterprises
Advanced threat actors such as nation-states, organized cybercriminals and cyber espionage actors represent the greatest information security threat to enterprises today. Many organizations struggle to detect these threats due to their clandestine nature, resource sophistication, and their deliberate "low and slow" approach to efforts.
For enterprises, these more sophisticated, organized and persistent threat actors are seen only by the digital traces they leave behind. For these reasons, enterprises need visibility beyond their network borders into advanced threats specifically targeting their organizations and infrastructure. This is known as threat intelligence.
Cyber threat researchers can begin by knowing a background profile of assets beyond the network border and being aware of offline threats such as those reported here by Luke Rodenheffer of Global Risk Insights. They should then monitor mission-critical IP addresses, domain names and IP address ranges (e.g., CIDR blocks).
This can grant advanced warning while adversaries are in the planning stages. With this enhanced visibility, you can gain improved insight into ongoing exploits, identification of cyber threats and the actors behind them. This allows you to take proactive steps to defend against these threats with an appropriate response.
SecureWorks Counter Threat Unit (CTU)™ is made up of a team of professionals with backgrounds in private security, military and intelligence communities, and has been publishing threat analyses since 2005. The CTU uses threat visibility across thousands of customer networks to identify emerging threats as well as many other resources including:
- Attack telemetry from clients
- Malware samples
- Investigations
- Public & private information sources
- Website monitoring
- Social media
- Communication channels used by threat actors
- Security community
- Government agencies
Data from these sources is fed into a threat intelligence management system that distills threat indicators such as:
- Attack signatures
- Domain names
- Host names
- IP addresses
- File names
- Registry data
- Vulnerabilities
- Catalogued malware
Threat indicators are then enriched with contextual Meta data to identify how they relate to threat actors and attack methods. The system then helps researchers identify relationships that would be impossible to find manually. Their research reveals who is attacking, how and why. This information then leads to actionable insights, such as:
What does the threat mean?
How do you resist?
What action should you take?
Intelligence knowledge-sharing occurs among leading cyber threat organizations, in both the public and private sectors. SecureWorks considers these to be the most informed and active organizations and is in constant communication with them. A partial list of these organizations is provided below:
- Forum of Incident Response and Security Teams (FIRST)
- National Cyber-Forensics & Training Alliance (NCFTA)
- Microsoft Active Protections Program (MAPP)
- Financial Services Information Sharing and Analysis Center (FS-ISAC)
- National Health Information Sharing & Analysis Center (NH-ISAC)
Cyber Threat Level
A Cyber Security Index (or threat level indicator) can be found on a variety of publicly available sources. Some of these indexes such as CyberSecurityIndex.org are updated via monthly surveys. Others such as NH-ISAC Threat Level or MS-ISAC Alert Level are updated more frequently based on shared global threat intelligence.
Most of these indexes follow the same format as the original SecureWorks CTU Cyber Security Index. It is evaluated daily by the CTU and updated as appropriate based on current threat activity. A reason provided for the index's current status will typically include reliable and actionable information about a threat targeting software, networks, infrastructures or key assets.
While the primary decision point for the Cyber Security Index is a "Daily Security Roundup and CSI Threat Level" discussion, the CTU can make decisions (with input from other senior security personnel from our Security Operations Centers, our CISO and other individuals) at any time day or night, depending on what events we see occurring or imminent.
When there is significant debate on what threat activity corresponds to which Cyber Security Index level, the CTU will utilize the criteria in the Cyber Security Index definitions in making decisions. The CTU takes a very serious and judicious approach when determining the Cyber Security Index.
The SecureWorks Cyber Security Index was previously published publicly, but is now only accessible to clients via the customer portal.
Threat Analyses
CTU research on cyber security threats, known as threat analyses, are publicly available. Of course, these are only released after the information is no longer helpful to the threat actors behind it. It is important not to show your cards when hunting down threat actors.
Emerging Threats
Threat advisories announce new vulnerabilities that can lead to emerging incidents. These are published as soon as possible in order to help anyone better secure their devices or systems.
Best Practices for Defense and Protection
Today's best practices for cyber security are a hybrid approach. Keeping up with rapid advancements in cyber threats roles that go beyond what is feasible for an in house security team to provide.
In-House IT Security Efforts:
- Strong end user education – compliance based practices for handling data, recognizing phishing attempts and procedures to counteract human engineering attempts
- Up to date software
- Firewall and anti-virus*
- IDS/IPS* – intrusion detection systems and intrusion prevention systems
- Security event monitoring*
- Incident response plan*
Security Partner Efforts:
- Penetration testing and vulnerability scanning
- Advanced threat monitoring of endpoints
- Always up to date threat intelligence
- Emergency incident response staff and investigators on call
*If resources are not available in-house, any of these efforts can be pushed to a managed security services provider.


No comments:
Post a Comment