Thursday, 14 February 2013
How to Recover an Encrypted Home Directory on Ubuntu
While the home-folder encryption in Ubuntu is far from a perfect solution (there is considerable data leakage from the swap file and the temp directory - for example once I've observed the flash videos from Chromium porn private browsing mode being present in the /tmp directory), it is a partial solution nevertheless and very easy to set up during installation. However what can you do if you need to recover the data because you dismantled your system?
Credit where credit is due: this guide is taken mostly from the Ubuntu wiki page. Also, this is not an easy "one-click" process. You should proceed carefully, especially if you don't have much experience with the command line.
Start Ubuntu (from a separate install, from the LiveCD, etc) and mount the source filesystem (this is usually as simple as going to the Places menu and selecting the partition). Start a terminal (Alt+F2 -> gnome-terminal) and navigate to the partitions home directory. Usually this will look like the following:
cd /media/9e6325c9-1140-44b7-9d8e-614599b27e05/home/
Now navigate to the users ecryptfs directory (things to note: it is ecryptfs not encryptfs and your username does not coincide with your full name - the one you click on when you log in)
cd .ecryptfs/username
The next step is to recovery your "mount password" which is different from the password you use to log in (when it asks you, type in the login password used for this account - for which you are trying to recover the data). Take note of the returned password (you can copy it by selecting it and pressing Shift+Ctrl+C if you are using the Gnome Terminal)
ecryptfs-unwrap-passphrase .ecryptfs/wrapped-passphrase
Now create a directory where you would like to mount the decrypted home directory:
sudo mkdir /media/decrypted
Execute the following and type in (or better - copy-paste) the mount password you've recovered earlier
sudo ecryptfs-add-passphrase --fnek
It will return something like the following. Take note of the second key (auth tok):
Inserted auth tok with sig [9986ad986f986af7] into the user session keyring
Inserted auth tok with sig [76a9f69af69a86fa] into the user session keyring
Now you are ready to mount the directry:
sudo mount -t ecryptfs /media/9e6325c9-1140-44b7-9d8e-614599b27e05/home/.ecryptfs/username/.Private /media/decrypted
Passphrase: # mount passphrase
Selection: aes
Selection: 16
Enable plaintext passthrough: n
Enable filename encryption: y # this is not the default!
Filename Encryption Key (FNEK) Signature: # the second key (auth tok) noted
You will probably get a warning about this key not being seen before (you can type yes) and asking if it should be added to your key cache (you should type no, since you won't be using it again probably).
That's it, now (assuming everything went right) you can access your decrypted folder in /media/decrypted. The biggest gotcha is that home/username/.Private is in fact a symlink, which - if you have an other partition mounted - will point you to the wrong directory, so you should use the home/.ecryptfs/username directory directly... If this does work you try this from this ubuntu tutorial ...
Or you can also try this Live CD method of opening a encrypted home directory
Monday, 28 January 2013
How to remove icons from Top-Taskbar on Gnome
You are using the Gnome-Classic interface - either you are using this by choice, or you are using the fallback mode which occurs if your graphics card & driver doesnt the 3D Acceleration required for the full Gnome-Shell GUI.
Press Win+Alt and right-click the top menu bar - N.B. Win is the Windows Symbol key
If you are not using Compiz then you need to :
Much more information is described in the linked Q&A and other links in that answer.
Wednesday, 23 January 2013
All You Need To Know About Linux Commands
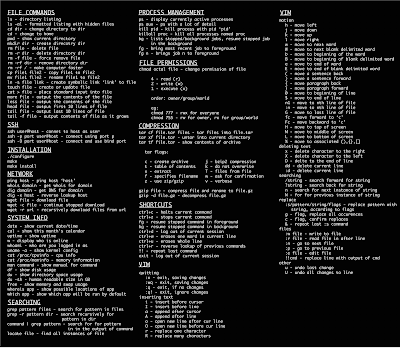
System Info
date – Show the current date and time
cal – Show this month's calendar
uptime – Show current uptime
w – Display who is online
whoami – Who you are logged in as
finger user – Display information about user
uname -a – Show kernel information
cat /proc/cpuinfo – CPU information
cat /proc/meminfo – Memory information
df – Show disk usage
du – Show directory space usage
free – Show memory and swap usage
Keyboard Shortcuts
Enter – Run the command
Up Arrow – Show the previous command
Ctrl + R – Allows you to type a part of the command you're looking for and finds it
Ctrl + Z – Stops the current command, resume with fg in the foreground or bg in the background
Ctrl + C – Halts the current command, cancel the current operation and/or start with a fresh new line
Ctrl + L – Clear the screen
command | less – Allows the scrolling of the bash command window using Shift + Up Arrow and Shift + Down Arrow
!! – Repeats the last command
command !$ – Repeats the last argument of the previous command
Esc + . (a period) – Insert the last argument of the previous command on the fly, which enables you to edit it before executing the command
Ctrl + A – Return to the start of the command you're typing
Ctrl + E – Go to the end of the command you're typing
Ctrl + U – Cut everything before the cursor to a special clipboard, erases the whole line
Ctrl + K – Cut everything after the cursor to a special clipboard
Ctrl + Y – Paste from the special clipboard that Ctrl + U and Ctrl + K save their data to
Ctrl + T – Swap the two characters before the cursor (you can actually use this to transport a character from the left to the right, try it!)
Ctrl + W – Delete the word / argument left of the cursor in the current line
Ctrl + D – Log out of current session, similar to exit
Learn the Commands
apropos subject – List manual pages for subject
man -k keyword – Display man pages containing keyword
man command – Show the manual for command
man -t man | ps2pdf - > man.pdf – Make a pdf of a manual page
which command – Show full path name of command
time command – See how long a command takes
whereis app – Show possible locations of app
which app – Show which app will be run by default; it shows the full path
Searching
grep pattern files – Search for pattern in files
grep -r pattern dir – Search recursively for pattern in dir
command | grep pattern – Search for pattern in the output of command
locate file – Find all instances of file
find / -name filename – Starting with the root directory, look for the file called filename
find / -name ”*filename*” – Starting with the root directory, look for the file containing the string
filename
locate filename – Find a file called filename using the locate command; this assumes you have already used the command updatedb (see next)
updatedb – Create or update the database of files on all file systems attached to the Linux root directory
which filename – Show the subdirectory containing the executable file called filename
grep TextStringToFind /dir – Starting with the directory called dir, look for and list all files containing TextStringToFind
File Permissions
chmod octal file – Change the permissions of file to octal, which can be found separately for user, group, and world by adding: 4 – read (r), 2 – write (w), 1 – execute (x)
Examples:
chmod 777 – read, write, execute for all
chmod 755 – rwx for owner, rx for group and world
For more options, see man chmod.
File Commands
ls – Directory listing
ls -l – List files in current directory using long format
ls -laC – List all files in current directory in long format and display in columns
ls -F – List files in current directory and indicate the file type
ls -al – Formatted listing with hidden files
cd dir – Change directory to dir
cd – Change to home
mkdir dir – Create a directory dir
pwd – Show current directory
rm name – Remove a file or directory called name
rm -r dir – Delete directory dir
rm -f file – Force remove file
rm -rf dir – Force remove an entire directory dir and all it’s included files and subdirectories (use with extreme caution)
cp file1 file2 – Copy file1 to file2
cp -r dir1 dir2 – Copy dir1 to dir2; create dir2 if it doesn't exist
cp file /home/dirname – Copy the file called filename to the /home/dirname directory
mv file /home/dirname – Move the file called filename to the /home/dirname directory
mv file1 file2 – Rename or move file1 to file2; if file2 is an existing directory, moves file1 into directory file2
ln -s file link – Create symbolic link link to file
touch file – Create or update file
cat > file – Places standard input into file
cat file – Display the file called file
more file – Display the file called file one page at a time, proceed to next page using the spacebar
head file – Output the first 10 lines of file
head -20 file – Display the first 20 lines of the file called file
tail file – Output the last 10 lines of file
tail -20 file – Display the last 20 lines of the file called file
tail -f file – Output the contents of file as it grows, starting with the last 10 lines
Compression
tar cf file.tar files – Create a tar named file.tar containing files
tar xf file.tar – Extract the files from file.tar
tar czf file.tar.gz files – Create a tar with Gzip compression
tar xzf file.tar.gz – Extract a tar using Gzip
tar cjf file.tar.bz2 – Create a tar with Bzip2 compression
tar xjf file.tar.bz2 – Extract a tar using Bzip2
gzip file – Compresses file and renames it to file.gz
gzip -d file.gz – Decompresses file.gz back to file
Printing
/etc/rc.d/init.d/lpd start – Start the print daemon
/etc/rc.d/init.d/lpd stop – Stop the print daemon
/etc/rc.d/init.d/lpd status – Display status of the print daemon
lpq – Display jobs in print queue
lprm – Remove jobs from queue
lpr – Print a file
lpc – Printer control tool
man subject | lpr – Print the manual page called subject as plain text
man -t subject | lpr – Print the manual page called subject as Postscript output
printtool – Start X printer setup interface
Network
ifconfig – List IP addresses for all devices on the local machine
ping host – Ping host and output results
whois domain – Get whois information for domain
dig domain – Get DNS information for domain
dig -x host – Reverse lookup host
wget file – Download file
wget -c file – Continue a stopped download
SSH
ssh user@host – Connect to host as user
ssh -p port user@host – Connect to host on port port as user
ssh-copy-id user@host – Add your key to host for user to enable a keyed or passwordless login
User Administration
adduser accountname – Create a new user call accountname
passwd accountname – Give accountname a new password
su – Log in as superuser from current login
exit – Stop being superuser and revert to normal user
Process Management
ps – Display your currently active processes
top – Display all running processes
kill pid – Kill process id pid
killall proc – Kill all processes named proc (use with extreme caution)
bg – Lists stopped or background jobs; resume a stopped job in the background
fg – Brings the most recent job to foreground
fg n – Brings job n to the foreground
Installation from source
./configure
make
make install
dpkg -i pkg.deb – install a DEB package (Debian / Ubuntu / Linux Mint)
rpm -Uvh pkg.rpm – install a RPM package (Red Hat / Fedora)
Stopping & Starting
shutdown -h now – Shutdown the system now and do not reboot
halt – Stop all processes - same as above
shutdown -r 5 – Shutdown the system in 5 minutes and reboot
shutdown -r now – Shutdown the system now and reboot
reboot – Stop all processes and then reboot - same as above
startx – Start the X system
Recommended reading:
Cheat-Sheets.org – All cheat sheets, round-ups, quick reference cards, quick reference guides and quick reference sheets in one page. The only one you need.
Tutorial: The best tips & tricks for bash, explained – Linux Tutorial Blog / Quality Linux tutorials without clutter
LinuxCommand.org – Learning the shell, Writing shell scripts, Script library, SuperMan pages, Who, What, Where, Why
LinuxManPages.com – General commands, System calls, Subroutines, Special files, File formats, Games, Macros and conventions, Maintenence commands, Most Popular Man Pages
Linux Newbie Guide: Shorcuts and Commands - Linux essential shortcuts and sanity commands; Common Linux commands - system info; Basic operations, network apps, file (de)compression; Process control; Basic administration commands, accessing drives/partitions; Network administration tools, music-related commands, graphics-related commands.
Monday, 21 January 2013
Tuesday, 8 January 2013
Got files separed from norm HTML
After meet up with team members we decide to migrate the site from norm HTML to PHP, the all projetc will take quite a while to finish, but so far the foundations, of the project are already laid down.. Quite interesting to see how this process is unfolding down ...
- Cut all the code and past in a separated document
- Save the new document with a different header name with .php file extension.
- Then import the content of the heading document into the main html document using the include* function - [ include is part of php library ]
Seems like all gone as we were expecting, but bear in mind that we faced some bugs when we tried to apply this approach the first time ... Here it goes the output still getting the original content but keeping all the information rendered on server..
Wednesday, 2 January 2013
Thursday, 13 December 2012
Using Virtual Ethernet Adapters in Promiscuous Mode on a Linux Host
VMware Workstation does not allow the virtual Ethernet adapter to go into promiscuous mode unless the user running VMware Workstation has permission to make that setting. This follows the standard Linux practice that only root can put a network interface into promiscuous mode.
When you install and configure VMware Workstation, you must run the installation as root. VMware Workstation creates the VMnet devices with root ownership and root group ownership, which means that only root has read and write permissions to the devices.
To set the virtual machine's Ethernet adapter to promiscuous mode, you must launch VMware Workstation as root because you must have read and write access to the VMnet device. For example, if you are using bridged networking, you must have access to /dev/vmnet0.
To grant selected other users read and write access to the VMnet device, you can create a new group, add the appropriate users to the group and grant that group read and write access to the appropriate device. You must make these changes on the host operating system as root (su -). For example, you can enter the following commands:
chgrp <newgroup> /dev/vmnet0
chmod g+rw /dev/vmnet0
<newgroup> is the group that should have the ability to set vmnet0 to promiscuous mode.
The command to run vmware workstations ads root is simple: user@user#:~$ sudo vmware start
If you want all users to be able to set the virtual Ethernet adapter (/dev/vmnet0 in our example) to promiscuous mode, run the following command on the host operating system as root:
chmod a+rw /dev/vmnet0
This is another posting showing "how to do computing" for everyday computer usages... For a general public
Subscribe to:
Comments (Atom)
Why PM2 Is Not Launching Your Node.js App—and How to Fix It
Why PM2 Is Not Launching Your Node.js App—and How to Fix It Broken Your Node.js PM2 — and How to Fix It Have you ever...
-
How To Hide and unhide the hard disk Volumes using CMD Commands : First check how many drives are there in my computer and then s...
-
In the rapidly evolving landscape of software development, the term " DevOps " has gained significant prominence. DevOps, short fo...
-
While learning Terraform some time back, I wanted to leverage Availability Zones in Azure. I was specifically looking at Virtual Machine Sca...